By: Jessica “Zhanna” Malekos Smith
Whether you are a cybersecurity professional, policymaker, or student, this article is a beginner’s guide to understanding the ‘musical scales’ of cyberwar. As such, it addresses what constitutes a use of force in cyberspace and how states may lawfully respond.
Understanding the legal confines of offensive and defensive cyber operations is a burgeoning area of study. In fact, as the former legal advisor to the U.S. State Department, Harold Koh, famously remarked at U.S. Cyber Command in 2012: “How do we apply old laws of war to new cyber-circumstances, staying faithful to enduring principles, while accounting for changing times and technologies?”[1]
To provide granularity in answering this question, this article uses the analogy of a piano keyboard. The accompanying graphic illustrates how the core principles of the law of war apply to cyberspace. Using the concept of Middle C and musical intervals known as octaves, it displays the range of permissible state conduct during times of conflict.
As the illustrious American poet, Henry Wadsworth Longfellow wrote, “music is the universal language of mankind.”[2] By juxtaposing the law of war with a keyboard, the process of how states evaluate the scale and effects of a cyber operation and determine a basis for resorting to a use of force under the Law of Armed Conflict (LOAC), can be more readily conceptualized.
Middle C – The Starting Position
Just as Middle C is the traditional starting position for beginner’s learning to play the piano, the United Nations (U.N.) Charter and customary international law can be similarly regarded as a state’s starting position for conducting peacetime military operations and combatant operations.[3] Even the 2016 U.S. White House Report on Legal Frameworks Governing Use of Military Force begins with using the Charter to determine an international legal basis in employing force.[4] The Charter is central to public international law, including the principles of jus ad bellum (the right to war) and jus in bello (the law in waging war). [5]
While these legal regimes govern all domains of war, can it be extended to include cyberspace? According to Robin Gei, a legal advisor to the International Committee of the Red Cross, since LOAC is “flexible enough to accommodate new technological developments” it applies equally to cyberspace.[6] Further, Gei offers parallel historical evidence of this by noting that the International Court of Justice considered the same issue when evaluating the legality of nuclear weapons.[7] Thus, while cyberspace is an artificial space that lacks traditional physical borders, the principles of LOAC still apply to this medium.[8] The central challenge remains, however, measuring how far the outer limits of this doctrine can be tested in cyberspace and yet still maintain its operative core.
In restricting a state’s use of force, Article 2(4) of the Charter states:
“All Members shall refrain in their international relations from the threat or use of force against the territorial integrity or political independence of any state, or in any other manner inconsistent with the Purposes of the United Nations.”[9]
Although there is no precise set of indicators for measuring a “use of force” in cyberspace, Koh identifies three examples of aggressive cyber activity that would constitute a use of force: “(1) operations that trigger a nuclear plant meltdown, (2) operations that open a dam above a populated area causing destruction, or (3) operations that disable air traffic control resulting in plane crashes.”[10]
Article 39 of the Charter also delineates the Security Council’s role in both determining “any threat to the peace, breach of the peace, or act of aggression” and offering recommendations on a proper course of action.[11] Walter Gary Sharp notes that this nexus demonstrates that “[e]very threat or use of force proscribed by Article 2(4) is a threat to international peace and security within the meaning of Article 39.”[12]
While no international consensus exists on defining a “cyber attack,”[13] the Tallinn Manual defines it as “a cyber operation, whether offensive or defensive, that is reasonably expected to cause injury or death to persons or damage or destruction to objects.”[14] A significant limitation to a state’s resort to force, however, is the right to self-defense from an “armed attack” under Article 51. It reads in relevant part:
“Nothing in the present Charter shall impair the inherent right of individual or collective self-defence if an armed attack occurs against a Member of the United Nations until the Security Council has taken measures necessary to maintain international peace and security.”[15]
But how is a use of force different from an armed attack?
A general good rule of thumb here, as Professor Michael N. Schmitt of the U.S. Naval War College suggests, is that “all armed attacks are uses of force, but not all uses of force qualify as armed attacks.”[16] This distinction is legally significant. The reason being, if a cyber operation does not satisfy the de minimus damage/injury threshold to constitute an “armed attack” under Article 51, then the victim state has two modes of recourse: “[1] the victim state may bring the matter before the Security Council, or [2] it may employ non-forcible countermeasures.”[17] And although Schmitt’s distinction between a use of force and armed attack represents the predominant view amongst the international community, the U.S. Government does not subscribe to it. Rather, from the U.S.’s standpoint, there is no legal difference between a use of force and an armed attack in the jus ad bellum.[18]
In summary, the Charter and customary law symbolize Middle C.
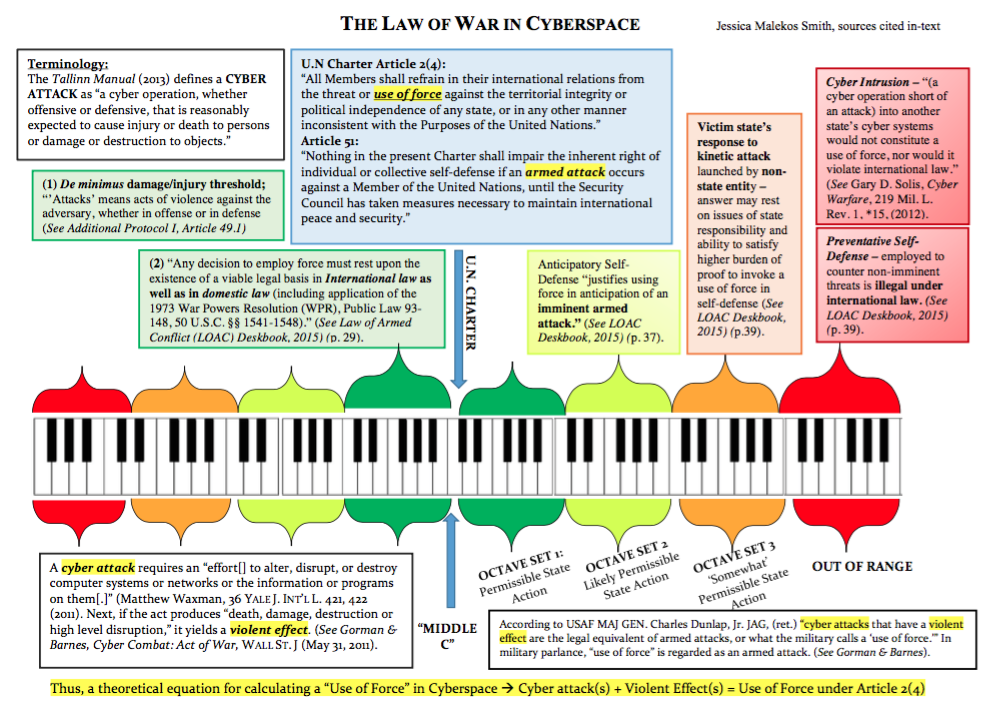 Octave Set 1: Evaluating an Armed Response to Cyber Operations
Octave Set 1: Evaluating an Armed Response to Cyber Operations
The green octave depicts the range of permissible action for a state that has fallen victim to a hostile cyber act. Rather than examine the scope of non-forcible countermeasures and economic sanctions here, the article’s chief focus is on evaluating an armed response.
As a first step, the victimized state must assess the amount of damage produced. This baseline analysis is necessary to determine if an armed response is justified. Second, it must identify the proper basis for employing force under international law. [19] Furthermore, if the U.S. were the victim state, any decision to employ a use of force must also comport with U.S. domestic laws like the 1973 War Powers Resolution.[20]
Pursuant to the U.S. Army’s Law of Armed Conflict Deskbook, the victim state must first determine whether the adversary’s action(s) constituted such high-level destruction amounting to an armed attack under de minimus damage/injury threshold. [21] The jus in bello definition of ‘attack’ is set forth in Additional Protocol I, Article 49.1, which describes such action as being “acts of violence against the adversary, whether in offense or in defense.”[22] Thus, if the military cyber operation satisfies the de minimus damage threshold to persons or property, then it qualifies as an attack. In military cyber operations, the jus in bello definition of an attack also imparts clarity in understanding what should constitute a cyber “armed attack” in the jus ad bellum.
If the requisite level of harm is not produced, however, then the hostile cyber act may qualify as a cyber intrusion.
The question then becomes, however, what constitutes a cyber intrusion? According to the laws of war, Professor Gary Solis of Georgetown University, a cyber intrusion is “a cyber operation short of an attack on another state’s cyber systems.” [23] Under this framework, acts of “cyber theft, intelligence gathering, espionage, or periodic disruptions or denials of nonessential cyber services”[24] would not constitute a use of force. Thus, in the absence of the requisite levels of death, destruction, or damage, as traditionally observed from kinetic attacks, cyber intrusions are generally not a use of force and do not violate LOAC.[25]
From a military perspective, retired U.S. Air Force Major General, Charles Dunlap Jr. reasons that “cyber attacks that have a violent effect are the legal equivalent of armed attacks, or what the military calls a ‘use of force.’”[26] While there is no fixed rule for calculating a use of force, as Koh explains, “most commentators focus on whether the direct physical injury and property damage resulting from the cyber event looks like that which would be considered a use of force.”[27]
On the other hand, prominent international legal scholars like Professor Matthew Waxman of Columbia University have advocated for less of a preoccupation with direct physical effects, and instead broadening the definition of a cyber attack to include the destruction or harmful degradation of data. For Waxman, a cyber attack requires an “effort to alter, disrupt, or destroy computer systems or networks or the information or programs on them[.]”[28]
While this area of law is unsettled, the predominant viewpoint amongst scholars is if the cyber act produces “death, damage, destruction or high- level disruption,”[29] it yields a violent effect and would qualify as use of force under Article 2(4).
Octave Set 2: Anticipatory Self-Defense in Cyberspace
The second octave in yellow depicts the range of state action that is likely to be permissible when evaluating a need for anticipatory self-defense. Here, the Army’s LOAC Deskbook provides that this category of defense “justifies using force in anticipation of an imminent armed attack.”[30]
The difference between a permissible act of anticipatory self-defense and an impermissible act of preventative self-defense lies in the state’s ability to demonstrate a decision by the aggressor state to attack it. For anticipatory self-defense to be lawful, there is a high standard of proof. This requirement goes beyond merely proffering evidence of a state’s hostile intent, but also evidence of some pending attack. To that end, the complexities of pairing evidentiary standards with attribution also make it difficult for a state to confidently identify a state’s hostile intent and plans of a pending attack in cyberspace.
Putting the attribution challenge aside, however, the following scenario is conditioned on the existence of proper attribution: Imagine that an Innocuous State I’s electrical grid was compromised by Nefarious State N and also accurately attributed to State N. In order for State I to be entitled to a use of force against State N under international law, Schmitt provides a three-part requirements test: the victim state’s opponent must have (1) “decided to actually exploit those [system] vulnerabilities; (2) the strike is likely to generate consequences at the armed attack level” and the victim state must “(3) act immediately to defend itself.”[31] Unless all three of these requirements are met, State I’s response would be restricted to only non-forceful responses such as economic sanctions or legal action.
Overall, state acts of self-defense must comply with the principles of necessity and proportionality. Necessity requires states to “consider the exhaustion or ineffectiveness of peaceful means of resolution, the nature of coercion applied by the aggressor State, the objectives of each party, and the likelihood of effective community intervention.”[32] Proportionality is met when states “limit the magnitude, scope, and duration of any use of force to that level of force which is reasonably necessary to counter a threat or attack.”[33]
Octave Set 3: Responding to a Kinetic Attack by Non-State Actors
The third orange octave depicts the range of state action that may be ‘somewhat’ permissible in responding to a kinetic attack launched by a non-state actor, like ISIS.
The reason why this octave is labeled – somewhat permissible – is that the surrounding circumstances, such as the scale and effects of the cyber operation and the legal status of the aggressor, will influence how the victim state may respond.
Here, the range of qualifying hostile cyber activity can range from “writing and executing malicious code, launching distributed denial of service [DDoS] attacks, providing malware or other cyber tools to a party to the conflict[.]”[34] The state’s analysis is further complicated when dealing with proxy cyber actors (i.e. digital strawmen), that may be clandestinely receiving financial or other material support from a state entity. In terms of the legal considerations at issue, under the Protocol Additional to the Geneva Conventions of 1949, the minority of the International Group of Experts is that malicious non-state cyber actors that do not qualify as a state-sponsored armed opposition group are unprivileged belligerents – i.e. “a civilian taking a direct part in hostilities.”[35] The majority view, including that of the U.S., however, does distinguish between civilians that engage in cyber operations during an armed conflict and unprivileged belligerents.[36] Under Rule 29 of The Tallinn Manual, civilians “are not prohibited from directly participating in cyber operations amounting to hostilities, but forfeit their protection from attacks for such time as they so participate.”[37] In contrast, the majority of the International Group of Experts held that unprivileged belligerents neither possess combatant immunity, nor a prisoner-of-war status.[38]
To how a state may respond to a cyber intrusion or attack, there is no requirement that a state respond using the same medium. Rather, from the perspective of Pentagon spokesman Colonel Dave Lapan, “[a] response to a cyber incident or attack on the US would not necessarily be a cyber-response. All appropriate options would be on the table . . . .”[39] The Army LOAC Deskbook reasons that how a victim state may respond to an armed attack “may rest on issues of state responsibility and ability to satisfy a higher burden of proof to invoke a use of force in self-defense.”[40] Moreover, according to Tallinn Paper No. 5, LOAC extends to “all cyber operations that have a nexus to the conflict, whether they are launched by states, non-state groups or individual hackers.”[41] In closing, how a victim state mounts a response will vary based on its evaluation of the surrounding circumstances, informational awareness, and mission readiness.
Out-of-Range Area: Impermissible State Action
The out-of-range area in red illustrates state action that is impermissible. Typically, such forms of prohibited state behavior include preventative self-defense and a use of armed force in response to a cyber intrusion. To be clear, preventative self-defense is force employed to counter non-imminent threats and is illegal under the customary international law.[42]
Recall that if a cyber operation satisfies the requisite de minimus damage threshold, then it qualifies as an attack. If it does not produce such harm to persons and/or property, then it may qualify as a cyber intrusion. Under this framework, an intrusion into another state’s cyber system to conduct espionage operations would not constitute a use of force.[43] Thus, absent the requisite level of death, destruction, or damage as traditionally observed from kinetic attacks, cyber intrusions do not violate LOAC.
Conclusion
By encouraging society to learn about the basic principles of the law of war in cyberspace, we can collectively better strategize ways to mitigate conflict in this domain. For each of us has a vital perspective to contribute as a cyber stakeholder. If music is indeed the universal language of mankind, then may the euphonious sound of peace always appeal to our ears.
With special thanks to Professor Eric Talbot Jensen of Brigham Young University Law School.
Jessica “Zhanna” Malekos Smith is a postdoctoral fellow with the Belfer Center’s Cyber Security Project at the Harvard Kennedy School. Previously she was a fellow of the Madeleine Korbel Albright Institute for Global Affairs in 2013. Malekos Smith received her B.A. from Wellesley College and J.D. from the University of California, Davis School of Law. She is an M.A. candidate in International Relations and Contemporary War at King’s College London, War Studies.
Notes:
[1] Harold Hongju Koh, International Law in Cyberspace, Yale University Faculty Scholarship Series. Paper 4854 (2012), http://digitalcommons.law.yale.edu/fss_papers/4854. (date accessed December 11, 2016).
[2] Henry Wadsworth Longfellow, BrainyQuote, https://www.brainyquote.com/quotes/quotes/h/henrywadsw379339.html (date accessed December 11, 2016).
[3] See Walter Gary Sharp, Sr. CyberSpace and the Use of Force, 68 (Aegis Research Corporation, 1999).
[4] Chris Mirasola and Helen Klein Murillo, A Summary of the U.S. White House Report on Legal Frameworks Governing Use of Military Force, Lawfare, (December 5, 2016), https://www.lawfareblog.com/summary-white-house-report-legal-frameworks-governing-use-military-force. (date accessed December 12, 2016).
[5] See Gary Solis, Cyber Warfare, 219 Mill. L. Rev 1, 10-11 (2014).
[6] See Robin Gei, The Conduct of Hostilities in and via Cyberspace, 104 Am. Soc’y Int’l L. Proc. 371, 371-72 (2010).
[7] See id.
[8] U.S. Dep’t of Def., Dep’t of Def. Directive No. 2311.01E, DoD Law of War Program (Feb. 22, 2011), http://dtic.mil/whs/directives/corres/pdf/231101e.pdf.
[9] U.N. Charter art. 2(4). (emphasis added).
[10] See Koh, supra note 2.
[11] U.N. Charter art. 39. (emphasis added).
[12] See Sharp, supra note 3 at 49.
[13] See Matthew C. Waxman, Cyber-Attacks and the Use of Force: Back to the Future of Article 2(4), 36 Yale J. Int’l L. 421, 433 (2011).
[14] See Tallinn Manual on International Law Applicable to Cyber Warfare, gen. ed. Michael N. Schmitt (New York: Cambridge University Press, 2013). [hereinafter Tallinn Manual]) (emphasis added).
[15] U.N. Charter art. 51. (emphasis added).
[16] See Michael N. Schmitt, Cyber Operations and the Jus Ad Bellum Revisited, 56 Vill. L. Review 569, 587, (2011).
[17] See Solis, supra note 4 at 15.
[18] See Koh, supra note 2. (explaining that “the United States has affirmed that established jus ad bellum rules do
apply to uses of force in cyberspace. I have also noted some clear-cut cases where the physical effects of a hostile cyber action would be comparable to what a kinetic action could achieve: for example, a bomb might break a dam and flood a civilian population, but insertion of a line of malicious code from a distant computer might just as easily achieve that same result.”)
[19] See David Lee et al., Law of Armed Conflict Deskbook, U.S. Army J. Advocate Gen.’s Legal Ctr. & Sch., Inter’l and Operational L. Dep’t 29 (2015), https://www.loc.gov/rr/frd/Military_Law/pdf/LOAC-Deskbook-2015.pdf [hereinafter Law of Armed Conflict Deskbook 2015]
[20] See id.
[21] See id.
[22] Protocol Additional to the Geneva Conventions of 12 August 1949, and relating to the Protection of Victims of International Armed Conflicts (Protocol I), 8 June 1977.
[23] See Solis, supra note 4 at 15.
[24] See id. at 21 (citing Michael N. Schmitt, The Law of Cyber Warfare: Quo Vadis, 25 1 Stan. L. POL. REV. 9, 11 (2015)).
[25] See id. (internal citation omitted here).
[26] See Siobhan Gorman & Julian E. Barnes, Cyber Combat: Act of War, Wall St. J. (May 31, 2011), http://www.wsj.com/articles/SB10001424052702304563104576355623135782718 (emphasis added).
[27] See Koh, supra note 2.
[28] See Waxman, supra note 10 at 422.
[29] See Gorman & Barnes, supra note 20.
[30] See Law of Armed Conflict Deskbook 2015, supra note 14 at 37.
[31] See Schmitt, supra note 13 at 592-3.
[32] See id. at 35.
[33] See id.
[34] See Solis, supra note 4 at 13 (quoting Laurie R. Blank, International Law and Cyber Threats from Non-State Actors, 89 Int’l. L. Stud. 406, 430 (2013).
[35] See Solis, supra note 4 at 13 (internal citation omitted here) (emphasis added).
[36] See Tallinn Manual, supra note 11 at 101.
[37] See id. at 104.
[38] See id. at 101.
[39] US Pentagon to treat cyber-attacks as ‘acts of war,’ BBC News (June 1, 2011), http://www.bbc.com/news/world-us-canada-13614125.
[40] See Law of Armed Conflict Deskbook 2015, supra note 14 at 39.
[41] See Michael N. Schmitt & Liis Vihul, The Nature of International Law Cyber Norms, NATO Coop. Cyber Def. Ctr. of excellence 8 (2014); see also Tallinn Manual, supra note 11, at 113-14.
[42] See id.
[43] See Solis, supra note 4 at 15.
Image credit: https://www.goodfreephotos.com/albums/vector-images/piano-keyboard-with-notes-vector-file.png
Feature image credit: https://www.goodfreephotos.com/albums/other-photos/hand-playing-keyboard-keys.jpg